Information Security
The information technology dissemination model changes with each passing day. If information security vulnerabilities are exploited by hackers and causes customer information to be leaked, it will further affect customers' trust or loyalty to the Company, or cause the Company to be fined or face other legal consequences for violating relevant laws and regulations. All of these situations might affect the Company's external image and reputation. Information security risk management and taking appropriate measures can effectively reduce the Company's potential financial losses and legal risks. It will also protect the Company's reputation and avoid potential negative impacts, creating a positive effect on protecting the economy, society and business partners, as well as the rights and interests of the Company and customers.
Therefore, Brogent continues to improve information security governance and strengthen information security capabilities. All information operations not only comply with international information security standards, but also comply with domestic and overseas laws and regulations on personal data protection and information security. The Company's information security unit is the Information Technology Department, and dedicated information security personnel are appointed in accordance with the "Information Security Management Guidelines for TWSE/TPEx-listed Companies." The department is responsible for formulating the Company's Information Security Policy, planning information security measures, and carrying out information security-related operations to ensure proper protection of the Company's confidential information, trade secrets, and personal data.
Information Security Policies
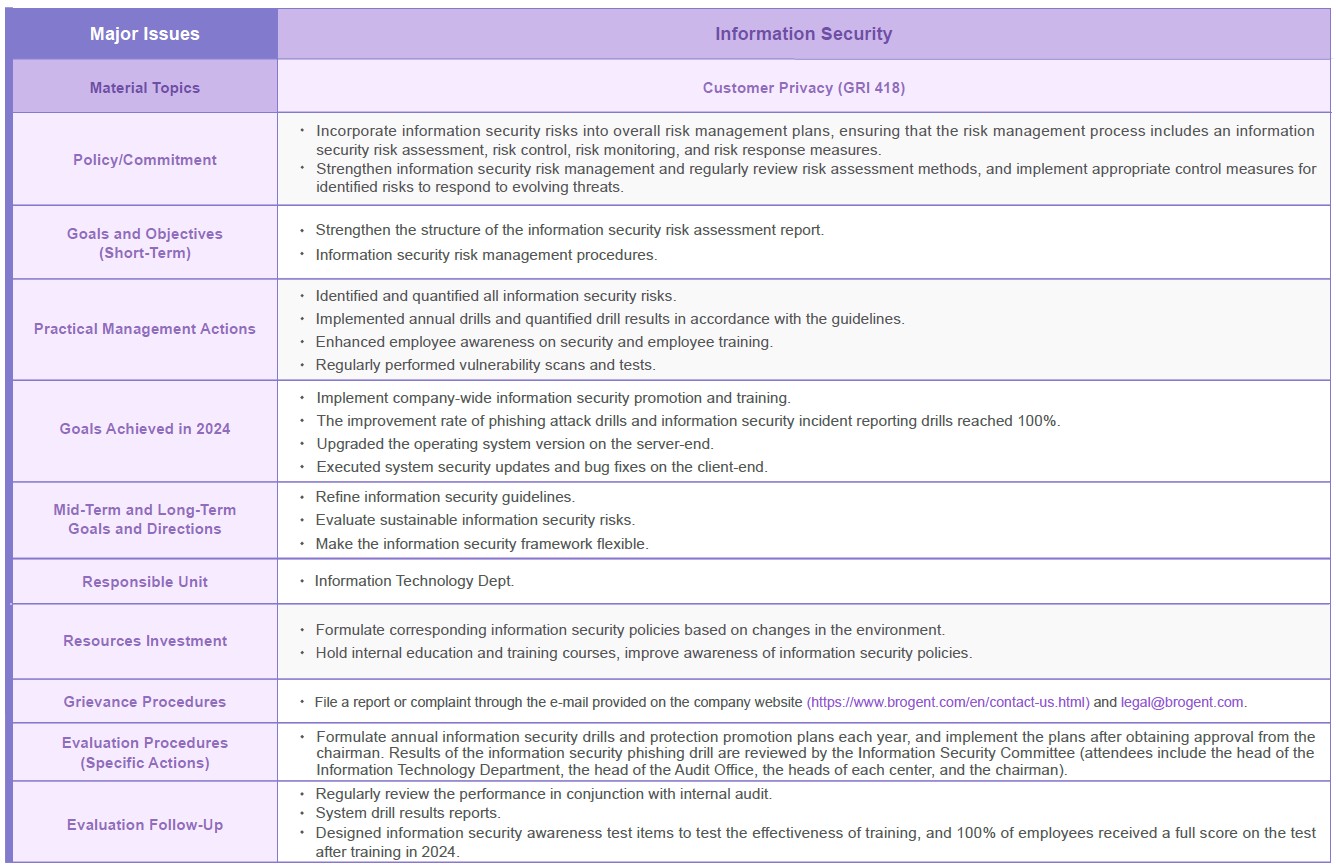
Ensure the confidentiality, integrity, availability, and compliance of the core system's management operations, and identify and assess qualitative or quantitative risks based on the importance of the assets, in order to control and verify the implementation effectiveness of information security management and whether information security goals are achieved.
Information Security Management Structure
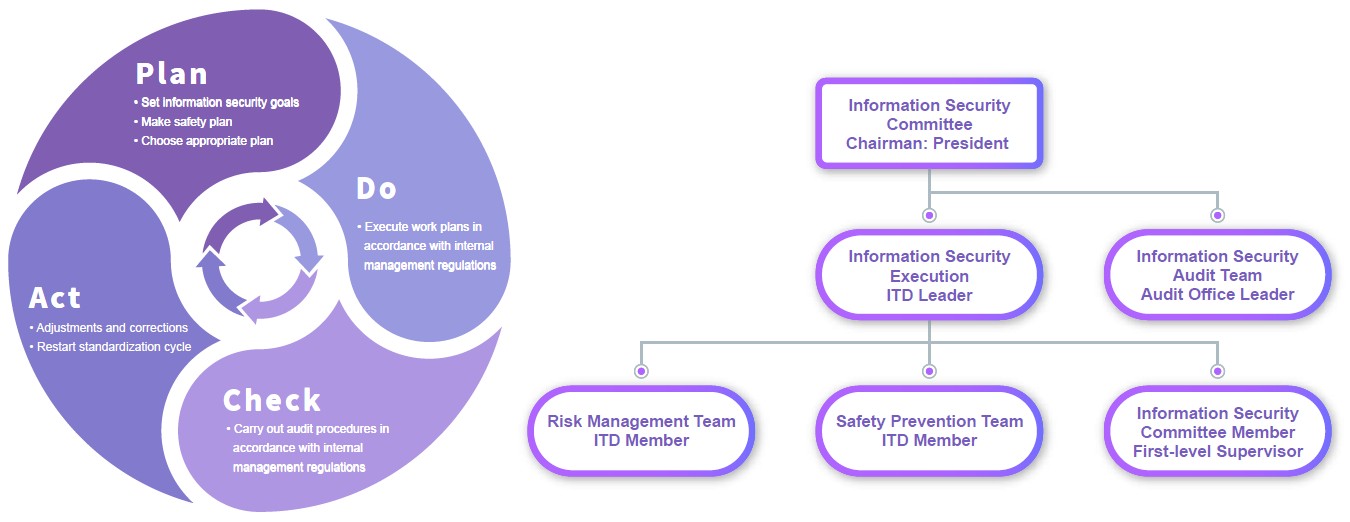
Brogent established the Information Security Committee to reduce the probability and impact of information security threats, and also improve the Company's ability to continue as a going concern. The president serves as the chairman of the committee, which meets once a year. We also referenced the spirit of ISO 27001 Information Security Management System, and use the PDCA cycle to ensure the achievement of information security management goals and continuous improvement.
In 2024, a total of 13 members of the Information Security Committee of Brogent. Convened 1 information security meeting to report on information security threats, drills, enhancements and the overall information security risk level. The total investment in information security is NT$5.44 million. The information security department conducts information security drills from time to time every year and strengthens employee information security education and training and publicity, so as to enhance personnel's awareness of information security risk; report to the Board of Directors on the implementation of information security on December 23, 2024.
Information Security Identification Process
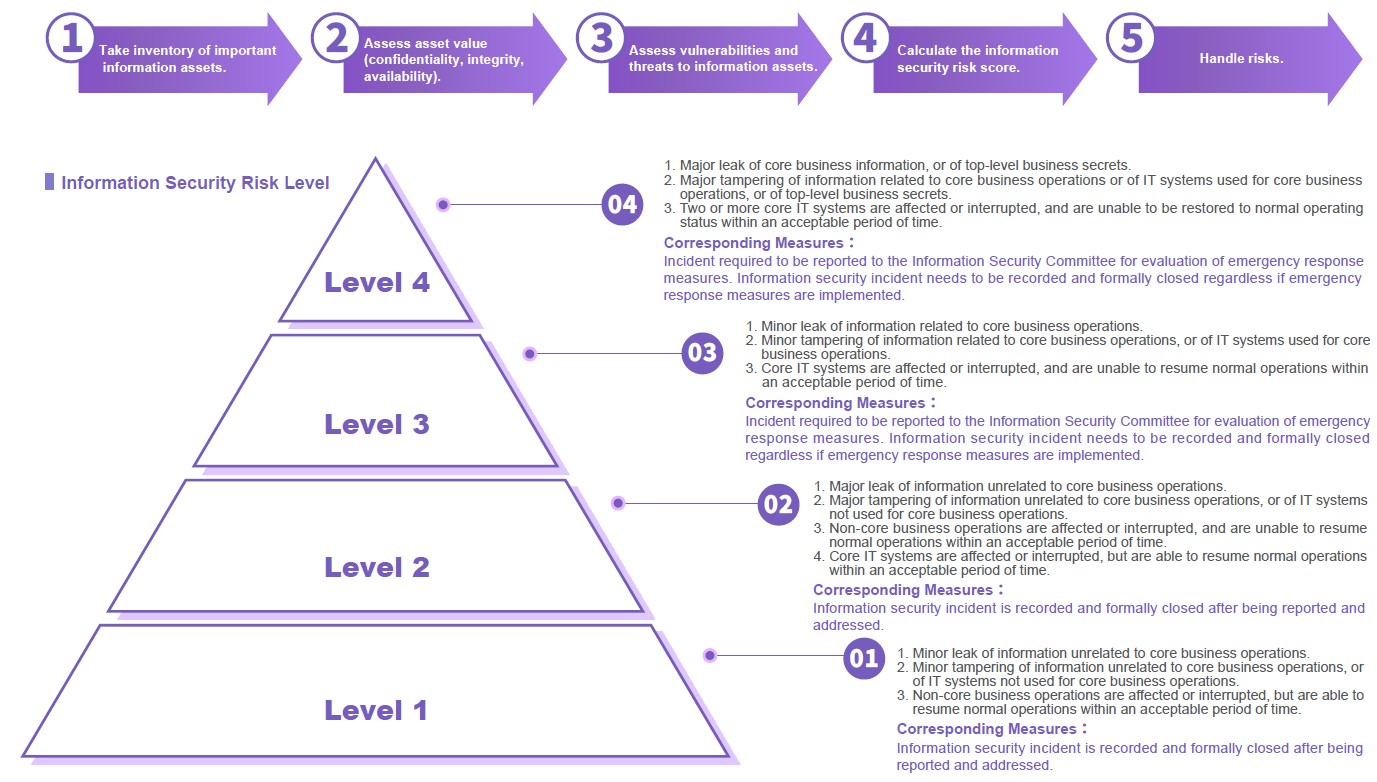
Information Security Measures
- Incorporate information security risks into overall risk management plans, ensuring that the risk management process includes an information security risk assessment, risk control, risk monitoring, and risk response measures.
- Improve employee safety awareness, education, and training, helping our employees to identify and respond to safety threats and risks. This includes providing our employees with the knowledge required to identify phishing emails, process personal information, and set strong passwords.
- Regularly performed vulnerability scans and tests to ensure the security of systems and applications. Regularly conducted disaster recovery drills to ensure rapid response and recovery when security incidents occur.
Improve Information Security Prevention Awareness
Brogent regularly plans annual information security drills and protection promotion plans every year. Attendees include the head of the Information Technology Department, the head of the Audit Office, the heads of each center, and the chairman. Results of the information security phishing drill are reviewed during the meeting. Brogent promotes the information security policy to all new employees. In addition to organizing information security awareness training every year, Brogent provides enhanced training for individuals with medium and high risk behavior during the phishing drill to identify risks. After the course, we designed information security awareness test items suitable for the Company's industry characteristics, environment, and culture according to testing standards for the telecommunications industry, in order to test the effectiveness of training, and 100% of employees received a full score on the test after training in 2024.

Customer Privacy
Brogent holds internal training courses to enhance employee awareness on protecting customer privacy and confidential information, and only use and protect customer information based on the contract signed with customers. Our Legal Department reviews contract content and the scope of information disclosed in each contract before marketing and disclosing customer information to the public, and legal advice will be provided to the marketing team on information disclosures. When customers discover that private or confidential information has been leaked, they can file a complaint or report through Brogent's official website (https://www.brogent.com/en/contact-us.html). No customer complaints of violating customer privacy or leakage of confidential information were received in 2024.Personal Data Protection
We promote personal data protection during the course on the "Employee Code of Conduct," and use actual cases to let employees understand the importance of personal data protection. The Personal Data Protection Task Force periodically examines whether the Company collects, processes, and uses personal data in accordance with the "Personal Data Protection and Management Rules," and destroys personal data that no longer needs to be retained each year.